2014-05-04 19:14:46 +00:00
# docker-postgis
2014-05-04 18:52:28 +00:00
2015-08-11 09:14:55 +00:00
2015-08-11 09:10:48 +00:00
2014-05-04 19:14:46 +00:00
A simple docker container that runs PostGIS
2019-01-25 12:57:23 +00:00
Visit our page on the docker hub at: https://hub.docker.com/r/kartoza/postgis/
2014-12-06 04:50:34 +00:00
2014-08-05 09:16:50 +00:00
There are a number of other docker postgis containers out there. This one
differentiates itself by:
* provides ssl support out of the box
* connections are restricted to the docker subnet
* template_postgis database template is created for you
2017-01-20 15:32:24 +00:00
* a default database 'gis' is created for you so you can use this container 'out of the
2014-08-05 09:16:50 +00:00
box' when it runs with e.g. QGIS
2019-01-25 12:57:23 +00:00
* replication support included
2014-08-05 09:16:50 +00:00
We will work to add more security features to this container in the future with
the aim of making a PostGIS image that is ready to be used in a production
environment (though probably not for heavy load databases).
2018-03-21 20:53:39 +00:00
There is a nice 'from scratch' tutorial on using this docker image on Alex Urquhart's
blog [here ](https://alexurquhart.com/post/set-up-postgis-with-docker/ ) - if you are
just getting started with docker, PostGIS and QGIS, we really recommend that you use it.
2015-08-11 09:14:55 +00:00
## Tagged versions
The following convention is used for tagging the images we build:
kartoza/postgis:[postgres_version]-[postgis-version]
So for example:
2018-03-21 20:53:39 +00:00
``kartoza/postgis:9.6-2.4`` Provides PostgreSQL 9.6, PostGIS 2.4
2015-08-11 09:14:55 +00:00
**Note:** We highly recommend that you use tagged versions because
successive minor versions of PostgreSQL write their database clusters
into different database directories - which will cause your database
to appear to be empty if you are using persistent volumes for your
database storage.
2014-09-10 11:17:37 +00:00
## Getting the image
2014-05-04 19:14:46 +00:00
2014-09-10 11:17:37 +00:00
There are various ways to get the image onto your system:
The preferred way (but using most bandwidth for the initial image) is to
get our docker trusted build like this:
```
docker pull kartoza/postgis
```
To build the image yourself without apt-cacher (also consumes more bandwidth
since deb packages need to be refetched each time you build) do:
2014-05-04 19:14:46 +00:00
```
2014-08-05 09:16:50 +00:00
docker build -t kartoza/postgis git://github.com/kartoza/docker-postgis
2014-05-04 19:47:26 +00:00
```
2019-01-25 12:57:23 +00:00
To build with apt-cacher (and minimise download requirements) you need to
2014-09-10 11:17:37 +00:00
clone this repo locally first and modify the contents of 71-apt-cacher-ng to
match your cacher host. Then build using a local url instead of directly from
github.
2014-05-04 19:47:26 +00:00
```
2014-09-10 11:17:37 +00:00
git clone git://github.com/kartoza/docker-postgis
2014-05-04 19:47:26 +00:00
```
Now edit ``71-apt-cacher-ng`` then do:
```
2014-05-04 20:31:00 +00:00
docker build -t kartoza/postgis .
2014-05-04 19:14:46 +00:00
```
2014-05-04 20:31:00 +00:00
## Run
2014-05-04 19:14:46 +00:00
To create a running container do:
```
2014-08-05 09:16:50 +00:00
sudo docker run --name "postgis" -p 25432:5432 -d -t kartoza/postgis
2014-05-04 19:14:46 +00:00
```
2016-09-06 07:15:07 +00:00
## Environment variables
2014-10-02 14:52:45 +00:00
You can also use the following environment variables to pass a
2017-01-20 15:32:24 +00:00
user name, password and/or default database name.
2014-10-02 14:52:45 +00:00
2014-12-05 16:00:20 +00:00
* -e POSTGRES_USER=< PGUSER >
* -e POSTGRES_PASS=< PGPASSWORD >
2017-01-20 15:32:24 +00:00
* -e POSTGRES_DBNAME=< PGDBNAME >
2014-10-02 14:52:45 +00:00
These will be used to create a new superuser with
your preferred credentials. If these are not specified then the postgresql
user is set to 'docker' with password 'docker'.
2016-09-06 07:14:20 +00:00
You can open up the PG port by using the following environment variable. By default
the container will allow connections only from the docker private subnet.
2019-01-25 12:57:23 +00:00
* -e ALLOW_IP_RANGE=< 0.0.0.0 / 0 > By default
t
Postgres conf is setup to listen to all connections and if a user needs to restrict which IP address
PostgreSQL listens to you can define it with the following environment variable. The default is set to listen to
all connections.
* -e IP_LIST=< *>
2016-09-06 07:14:20 +00:00
2018-03-21 20:53:39 +00:00
## Convenience docker-compose.yml
2014-10-02 14:52:45 +00:00
2018-03-21 20:53:39 +00:00
For convenience we have provided a ``docker-compose.yml`` that will run a
copy of the database image and also our related database backup image (see
[https://github.com/kartoza/docker-pg-backup ](https://github.com/kartoza/docker-pg-backup )).
2014-10-02 14:52:45 +00:00
2018-03-21 20:53:39 +00:00
The docker compose recipe will expose PostgreSQL on port 25432 (to prevent
potential conflicts with any local database instance you may have).
2014-10-02 14:52:45 +00:00
Example usage:
```
2018-03-21 20:53:39 +00:00
docker-compose up -d
2014-10-02 14:52:45 +00:00
```
2018-03-21 20:53:39 +00:00
**Note:** The docker-compose recipe above will not persist your data on your local
disk, only in a docker volume.
2014-05-04 19:14:46 +00:00
## Connect via psql
Connect with psql (make sure you first install postgresql client tools on your
host / client):
```
psql -h localhost -U docker -p 25432 -l
```
2014-05-04 20:31:00 +00:00
**Note:** Default postgresql user is 'docker' with password 'docker'.
2014-05-04 19:14:46 +00:00
You can then go on to use any normal postgresql commands against the container.
2019-01-25 12:57:23 +00:00
Under ubuntu 16.04 the postgresql client can be installed like this:
2014-05-04 19:14:46 +00:00
```
2019-01-25 12:57:23 +00:00
sudo apt-get install postgresql-client-9.6
2014-05-04 19:14:46 +00:00
```
2014-05-04 20:31:00 +00:00
## Storing data on the host rather than the container.
2014-05-04 19:14:46 +00:00
Docker volumes can be used to persist your data.
```
mkdir -p ~/postgres_data
docker run -d -v $HOME/postgres_data:/var/lib/postgresql kartoza/postgis`
```
2015-08-08 12:11:45 +00:00
You need to ensure the ``postgres_data`` directory has sufficient permissions
2014-05-04 19:14:46 +00:00
for the docker process to read / write it.
2018-03-21 20:53:39 +00:00
## Postgres Replication Setup
2018-03-22 07:06:45 +00:00
Replication allows you to maintain two or more synchronised copies of a database, with a
single **master** copy and one or more **replicant** copies. The animation below illustrates
this - the layer with the red boundary is accessed from the master database and the layer
with the green fill is accessed from the replicant database. When edits to the master
2019-01-25 12:57:23 +00:00
layer are saved, they are automatically propagated to the replicant. Note also that the
2018-03-22 07:06:45 +00:00
replicant is read-only.
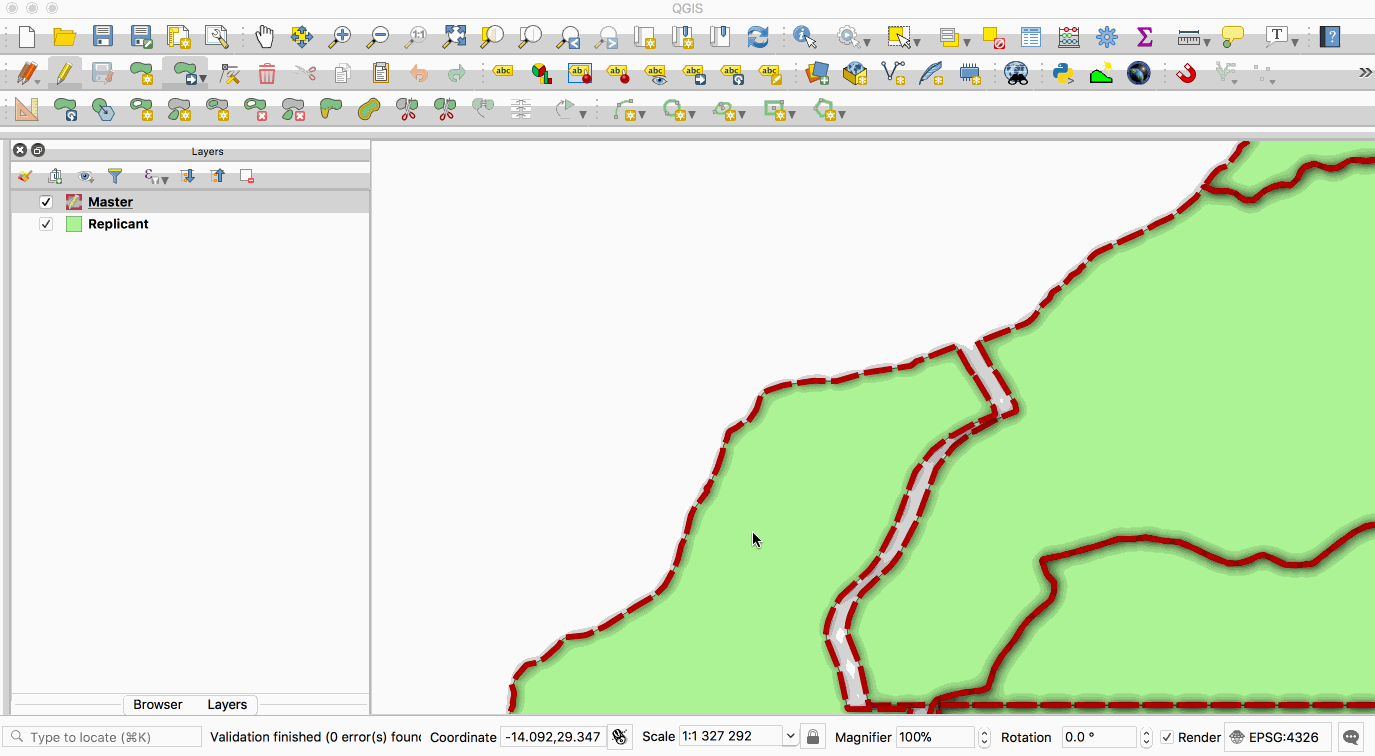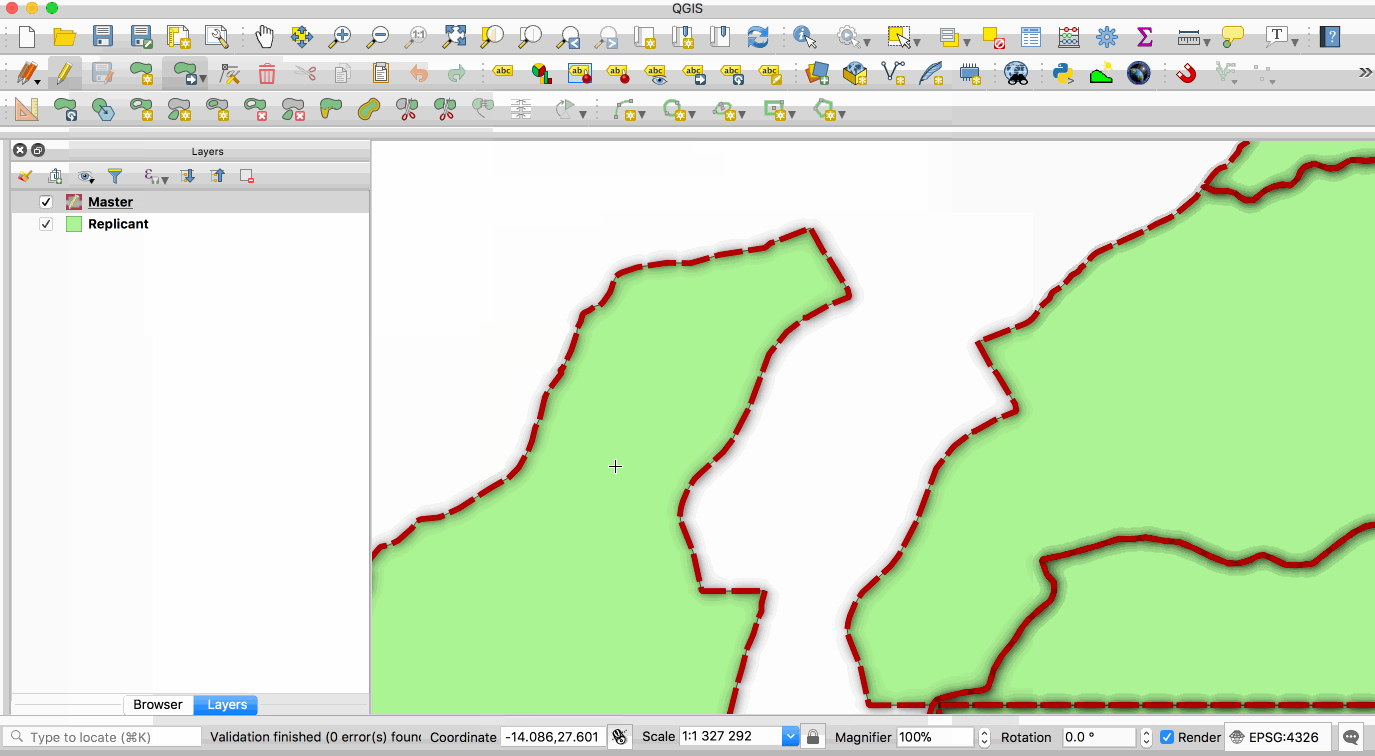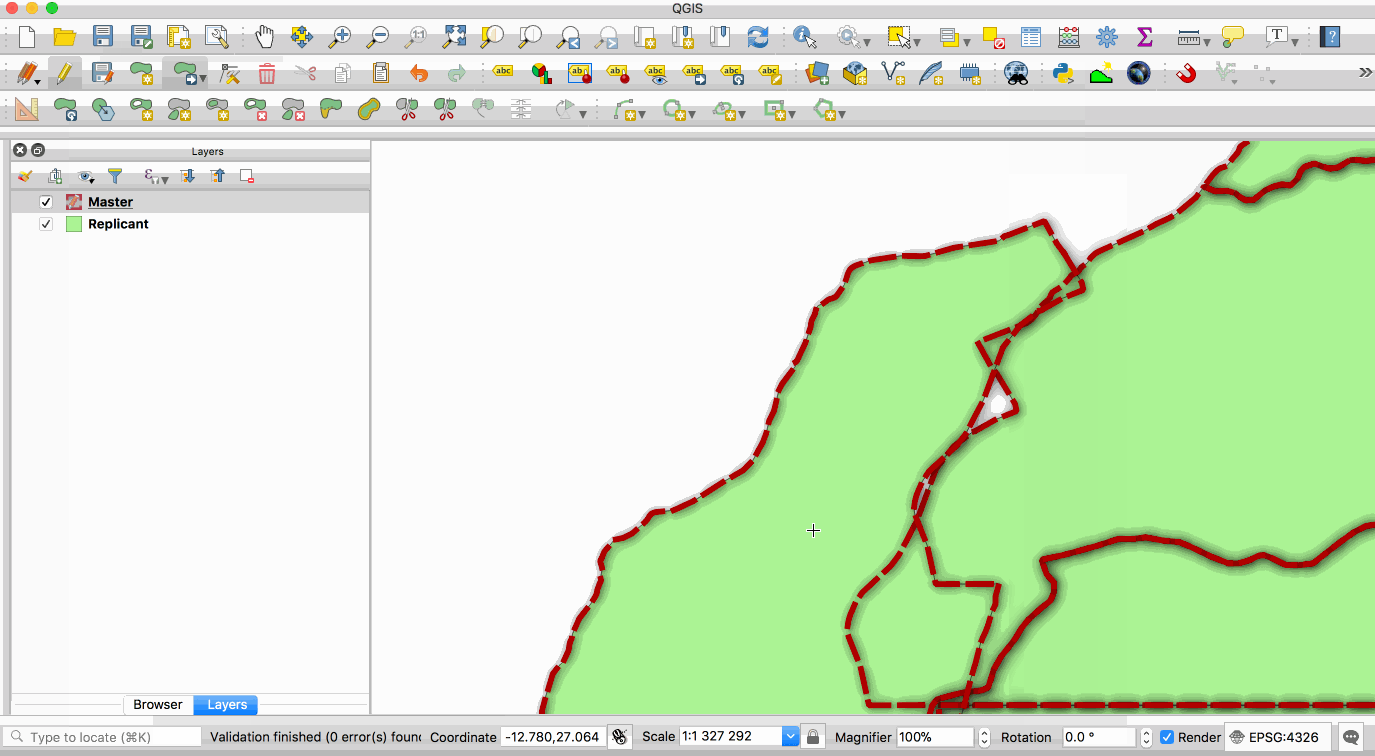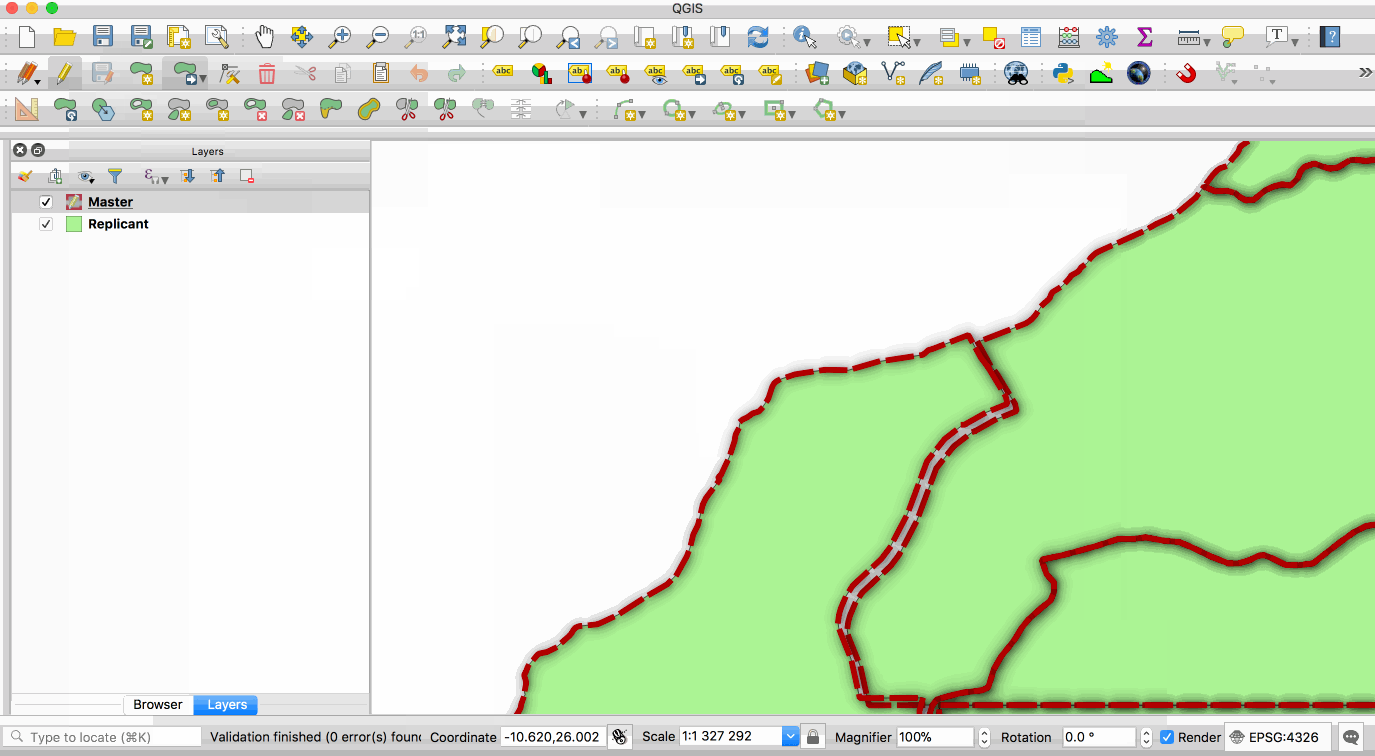
This image is provided with replication abilities. We can
categorize an instance of the container as `master` or `replicant` . A `master`
2019-01-25 12:57:23 +00:00
instance means that a particular container has a role as a single point of
2018-03-22 07:06:45 +00:00
database write. A `replicant` instance means that a particular container will
2018-03-21 20:53:39 +00:00
mirror database content from a designated master. This replication scheme allows
2019-01-25 12:57:23 +00:00
us to sync databases. However a `replicant` is only for read-only transaction, thus
we can't write new data to it. The whole database cluster will be replicated.
2018-03-21 20:53:39 +00:00
To experiment with the replication abilities, you can see a (docker-compose.yml)[sample/replication/docker-compose.yml]
2019-01-25 12:57:23 +00:00
sample. There are several environment variables that you can set, such as:
2018-03-21 20:53:39 +00:00
Master settings:
2019-01-25 12:57:23 +00:00
- **ALLOW_IP_RANGE**: A pg_hba.conf domain format which will allow specified host(s)
to connect into the container. This is needed to allow the `slave` to connect
into `master` , so specifically this settings should allow `slave` address. It is also needed to allow clients on other hosts to connect to either the slave or the master.
- Both POSTGRES_USER and POSTGRES_PASS will be used as credentials for the slave to
connect, so make sure you change this into something secure.
2018-03-21 20:53:39 +00:00
Slave settings:
2019-01-25 12:57:23 +00:00
- **REPLICATE_FROM**: This should be the domain name or IP address of the `master`
instance. It can be anything from the docker resolved name like that written in the sample,
2018-03-21 20:53:39 +00:00
or the IP address of the actual machine where you expose `master` . This is
useful to create cross machine replication, or cross stack/server.
2018-03-22 07:06:45 +00:00
- **REPLICATE_PORT**: This should be the port number of `master` postgres instance.
2018-03-21 20:53:39 +00:00
Will default to 5432 (default postgres port), if not specified.
2019-01-25 12:57:23 +00:00
- **DESTROY_DATABASE_ON_RESTART**: Default is `True` . Set to 'False' to prevent
2018-03-22 07:06:45 +00:00
this behaviour. A replicant will always destroy its current database on
2018-03-21 20:53:39 +00:00
restart, because it will try to sync again from `master` and avoid inconsistencies.
2019-01-25 12:57:23 +00:00
- **PROMOTE_MASTER**: Default none. If set to any value then the current replicant
2018-03-21 20:53:39 +00:00
will be promoted to master.
2019-01-25 12:57:23 +00:00
In some cases when the `master` container has failed, we might want to use our `replicant`
as `master` for a while. However, the promoted replicant will break consistencies and
is not able to revert to replicant anymore, unless it is destroyed and resynced
2018-03-21 20:53:39 +00:00
with the new master.
2019-01-25 12:57:23 +00:00
To run the sample replication, follow these instructions:
2018-03-21 20:53:39 +00:00
2019-01-25 12:57:23 +00:00
Do a manual image build by executing the `build.sh` script
2018-03-21 20:53:39 +00:00
```
./build.sh
```
2019-01-25 12:57:23 +00:00
Go into the `sample/replication` directory and experiment with the following Make
2018-03-21 20:53:39 +00:00
command to run both master and slave services.
```
make up
```
To shutdown services, execute:
```
make down
```
To view logs for master and slave respectively, use the following command:
```
make master-log
make slave-log
```
You can try experiment with several scenarios to see how replication works
2018-03-22 07:06:45 +00:00
### Sync changes from master to replicant
2018-03-21 20:53:39 +00:00
You can use any postgres database tools to create new tables in master, by
connecting using POSTGRES_USER and POSTGRES_PASS credentials using exposed port.
2019-01-25 12:57:23 +00:00
In the sample, the master database was exposed on port 7777.
2018-03-21 20:53:39 +00:00
Or you can do it via command line, by entering the shell:
```
make master-shell
```
Then made any database changes using psql.
2019-01-25 12:57:23 +00:00
After that, you can see that the replicant follows the changes by inspecting the
slave database. You can, again, use database management tools using connection
2018-03-22 07:06:45 +00:00
credentials, hostname, and ports for replicant. Or you can do it via command line,
2018-03-21 20:53:39 +00:00
by entering the shell:
```
make slave-shell
```
Then view your changes using psql.
2018-03-22 07:06:45 +00:00
### Promoting replicant to master
2018-03-21 20:53:39 +00:00
2019-01-25 12:57:23 +00:00
You will notice that you cannot make changes in replicant, because it is read-only.
2018-03-21 20:53:39 +00:00
If somehow you want to promote it to master, you can specify `PROMOTE_MASTER: 'True'`
into slave environment and set `DESTROY_DATABASE_ON_RESTART: 'False'` .
2018-03-22 07:06:45 +00:00
After this, you can make changes to your replicant, but master and replicant will not
2019-01-25 12:57:23 +00:00
be in sync anymore. This is useful if the replicant needs to take over a failover master.
However it is recommended to take additional action, such as creating a backup from the
slave so a dedicated master can be created again.
2018-03-21 20:53:39 +00:00
2018-03-22 07:06:45 +00:00
### Preventing replicant database destroy on restart
2018-03-21 20:53:39 +00:00
You can optionally set `DESTROY_DATABASE_ON_RESTART: 'False'` after successful sync
2019-01-25 12:57:23 +00:00
to prevent the database from being destroyed on restart. With this setting you can
shut down your replicant and restart it later and it will continue to sync using the existing
database (as long as there are no consistencies conflicts).
2014-05-04 19:14:46 +00:00
2018-03-21 20:53:39 +00:00
However, you should note that this option doesn't mean anything if you didn't
2019-01-25 12:57:23 +00:00
persist your database volume. Because if it is not persisted, then it will be lost
2018-03-21 20:53:39 +00:00
on restart because docker will recreate the container.
2014-05-04 19:14:46 +00:00
2014-05-04 20:31:00 +00:00
## Credits
2014-08-05 09:16:50 +00:00
Tim Sutton (tim@kartoza.com)
2019-01-25 12:57:23 +00:00
Gavin Fleming (gavin@kartoza.com)
Risky Maulana (rizky@kartoza.com)
Admire Nyakudya (admire@kartoza.com)
December 2018